A client recently contacted us about emails being sent from a Gmail account to contacts in her address book. Somehow a user had managed to gain access to her account and was attempting to SPAM contacts by sending emails from the client's email address - hoping that being sent from a familiar address, the recipient was likely to click on the link in the email. In this case, the client was lucky that no damage was done to her account and that her emails remained in-tact. But it begs the question: Imagine losing access to your email account and everything in it! Fortunately, there are steps you can take to better protect your email account.
With so many services now operating online, it has become easier than you think for someone to gain access to your digital accounts. Sometimes, a simple password can be easily guessed, while other times, downloaded software or malicious emails can gain access to your accounts. Either way, using only a password to protect your email is not always the best way to secure your account.
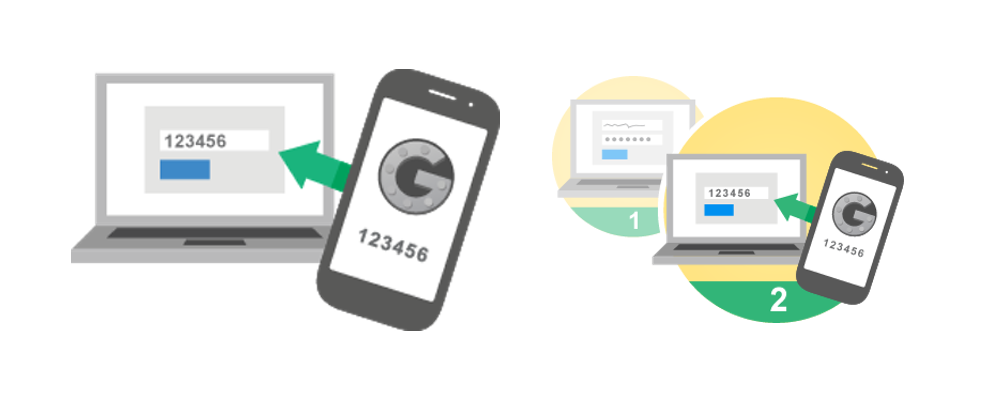
2-Step authentication is a process whereby you use both a password and your phone (either through SMS or in-app notifications) to access your account and adds a significant level of security to your account. In summary, you log into your account with your password, but then are required to enter a code (sent to your mobile) to verify your login. So even if someone gains access to your password, they will not be able to access your account.
In some instances, you can add a "trusted computer" - allowing you to bypass this process on specific devices. This will still protect you as if anyone else tries to lo into your account from anther computer, they will still be required to use the 2-Step authentication.
You can find out more about Gmail's 2-Step Authentication at the following link:
https://www.google.com.au/landing/2step/
While this article refers to Gmail's 2-Step Authentication, there are a large number of cloud-based services using similar systems. If available, you should always choose this method of authentication as an additional layer of security over your accounts.
To find out more about protecting your accounts online, or to discuss more about cloud-based services, please Contact Us.
Get updates, tips and industry news delivered directly to you